Pentest Home Lab - 0x3 - Kerberoasting: Creating SPNs so you can roast them
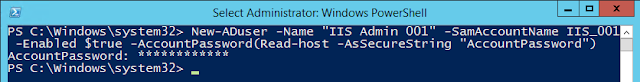
TL;DR There are a lot of great blogs out there that show you how to Kerberoast. In this post, I'm going to walk through the process of setting up your lab so that you can practice this attack. This involves creating a domain user and then mapping a SPN to that account. After that, I'll walk through using Empire to launch Invoke-Kerberoast, and I'll crack the hashes offline with Hashcat. Pentest Home Lab Recap If you don't already have an Active Directory lab and want to build one so that you can play along, check out my previous posts: Pentest Home Lab - 0x0 - Building A Virtual Corporate Domain Pentest Home Lab - 0x1 - Building Your AD Lab on AWS Pentest Home Lab - 0x2 - Building Your AD Lab on Premises using Proxmox VE The Attack: Kerberoasting Attack Goals Domain privesc & lateral movement. If you have domain credentials and access to the domain, this is a relatively easy way to gain additional access within the domain. If all goes well, you