Crossdomain.xml can be overly permissive even without a wildcard (*)
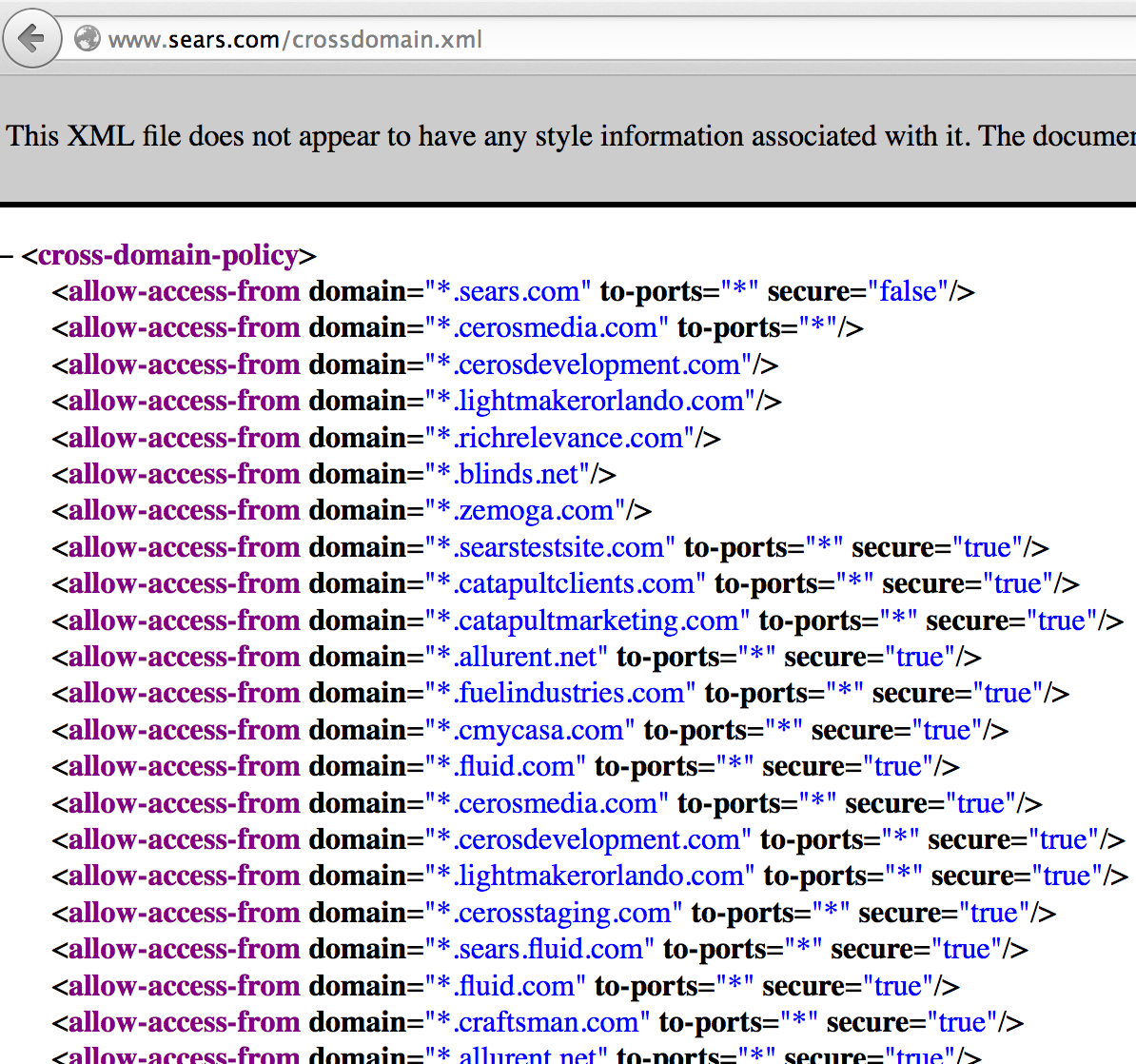
Before too much time passes, I want to write about a point I covered in my presentation that is not widely covered on the web -- or maybe not even covered at all. The main point is that even if you have a very specific list of domains that you trust, you may still be vulnerable to CWE-942 , if one of the domains that you trust is available for purchase. To illustrate this point in my talk, I used the crossdomain.xml file at www.sears.com: What I found in my research is that there are plenty of crossdomain.xml files that trust sites that are available for purchase. As far as I know, every single security assessment tool out there would pass right over these sites, missing the fact that a vulnerable configuration could be in place. In the case of www.sears.com, they are trusting the domain: searstestsite.com. For the purpose of demonstrating the vulnerability, I purchased this domain. This means that I can now host a malicious SWF at www.searstestsite.com, a domain that I o