CVE-2014-2226
Ubiquiti - UniFi Controller - Admin/root password hash sent via syslog
Misuse case:
An attacker who has access to network traffic between the UniFi controller and the configured syslog server, can retrieve the password hash and use it to access all managed access points, and potentially the UniFi controller as well.
Details:
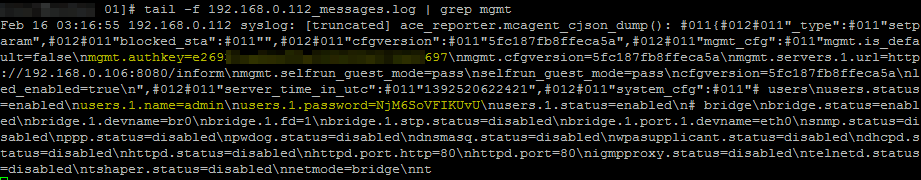
If remote logging is enabled on the UniFi controller, the controller sends syslog messages to the configured syslog server. Contained within the syslog messages is the admin password hash that is used by both the UniFi controller, and all managed Access Points.
Additional details:
Misuse case:
An attacker who has access to network traffic between the UniFi controller and the configured syslog server, can retrieve the password hash and use it to access all managed access points, and potentially the UniFi controller as well.
Details:
If remote logging is enabled on the UniFi controller, the controller sends syslog messages to the configured syslog server. Contained within the syslog messages is the admin password hash that is used by both the UniFi controller, and all managed Access Points.
In the screenshot below, the auth key and the encrypted password are highlighted in yellow.
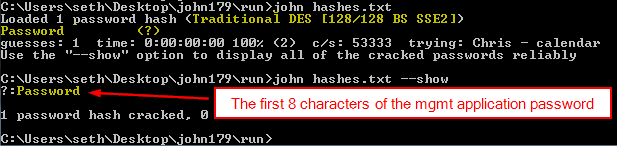
The password is encrypted using the legacy crypt(1) utility, which uses Traditional DES [128/128 BS SSE2], and can be recovered using John the Ripper:
Note: The salt (and hash) changes each time the message is sent, but the password can always be recovered.
Once you crack the password, you can log into any of the managed access points via SSH. This is actually the format of the password that is used by BusyBox:

The CVE was assigned as there is no utility (reason) for sending the admin password via syslog messages.
Additional details:
(CVE-2014-2226) - Ubiquiti Networks - UniFi Controller - Admin/root password hash sent via syslog
-----------
Vendor:
-----------
Ubiquiti Networks (http://www.ubnt.com/)
----------------------------------------------
Affected Products/Versions:
----------------------------------------------
UniFi Controller v2.4.6
Note: Previous versions may be affected
-----------------
Description:
-----------------
Title: Admin/Root password hash sent in syslog messages
CVE: CVE-2014-2226
CWE: CWE-319: http://cwe.mitre.org/data/definitions/319.html
Researcher: Seth Art - @sethsec
If remote logging is enabled on the UniFi controller, syslog messages are sent to a syslog server. Contained within the syslog messages is the admin password that is used by both the UniFi controller, and all managed Access Points. This CVE was assigned as there is no utility for sending the admin password hash via syslog messages.
------
POC:
------
Not Applicable.
-------------
Solution:
-------------
UniFi Controller - Upgrade to UniFi Controller v3.2.1 or greater
-----------------------------
Disclosure Timeline:
-----------------------------
2014-02-16: Notified Ubiquiti of vulnerabilities in UniFi and mFi products
2014-02-17: Ubiquiti acknowledges and requests details
2014-02-17: Report with POC sent to Ubiquiti
2014-02-19: Asks Ubiquiti to confirm receipt of report
2014-02-19: Ubiquti confirms receipt of report and existence of the vulnerabilities
2014-02-28: CVE-2014-2226 assigned
2014-03-12: Requested status update
2014-03-27: Requested status update
2014-04-07: Requested status update
2014-04-09: Ubiquiti provides timeline for solution
2014-05-30: Requested status update
2014-06-12: Requested status update
2014-06-12: UniFi 3.2.1 is released
2014-06-13: Set public disclosure date of 2014-07-24
2014-07-24: Public disclosure


Comments